Identity & Access Management Services
IAM Strategy
IAM Roadmap
IAM Assessment
IAM Governance
Architecture & Design
Identity & Access Management Services
IAM Strategy
IAM Roadmap
IAM Assessment
IAM Governance
Architecture & Design
Expert Identity Management Services
IAM Implementation
Idenhaus has extensive experience implementing complex Identity and Access solutions for large enterprises. Organizations that partner with Idenhaus benefit from our experienced consultants and proven delivery methodology, reducing risk and optimizing results.
Our IDM implementation team can help you with:
- Developing IAM Requirements and Solution Design
- Implementing your IAM solution
- Integration with HRIS systems – align process, policy, and data models
- Integration with Active Directory and Applications
- Federation
- Multi-factor authentication
- Privileged Access Management
- Role Based Access Control
- Stakeholder alignment and buy-in
- Testing and Production deployment
We provide our customers with a strong technical foundation for their IAM solution that is robust, scalable, and delivers business value.
Most organizations approach identity and access management projects tactically, rather than stepping back and determining a course of action that will solve enterprise-wide issues. Starting with a tactical approach is both short-sighted and high risk, leading to failed projects, unnecessary expense, and the delay of beneficial results. A cohesive Identity Management strategy provides a context for individual projects (e.g. user provisioning, directory consolidation), which will then be seen as a supporting element of a unified plan that has impact at an enterprise level.
Key Activities/Deliverables:
- Conduct business & technical stakeholder interviews
- Identify & prioritize all identified IDM opportunities
- Create phased approach to implement opportunities
- Develop IAM solution Roadmap
- Build IAM business case
- Present IAM strategy & High-level Roadmap to leadership
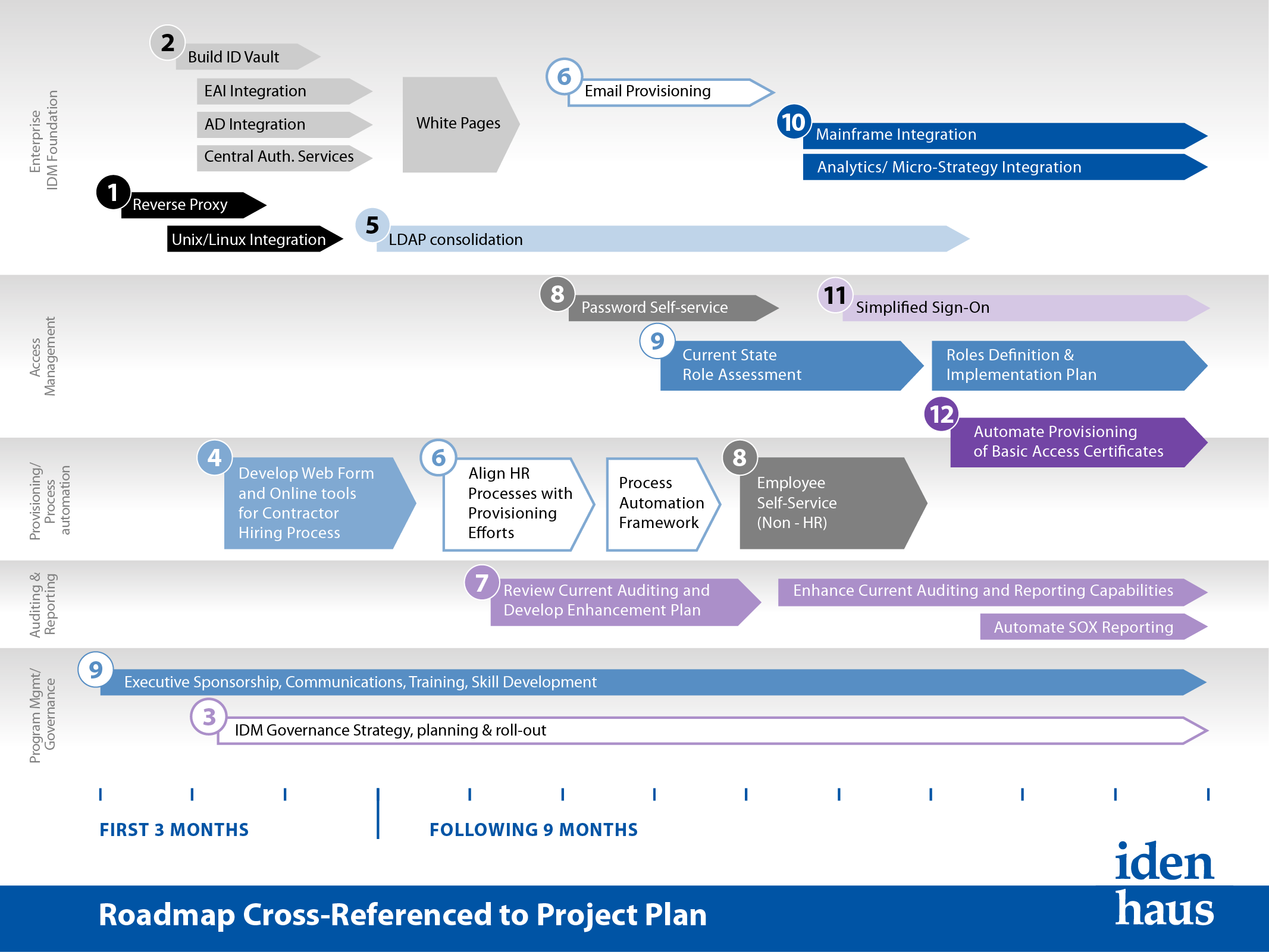
IAM Roadmap
An Identity and Access Roadmap is developed in collaboration with the client based on current state and the desired end state. This engagement is a lightweight version of a Strategy engagement and will provide high-level recommendations around IAM systems/architecture and existing provisioning processes. Lastly, the Road Map engagement will define a high level plan for implementing short, mid, and long term IAM components that addresses both tactical and strategic objectives.
- Conduct interviews with a small group of stakeholders
- Identify & prioritize key IAM opportunities
- Create phased approach to implement key IAM opportunities
- Develop & Present Road Map to leadership
- Product evaluation / recommendation
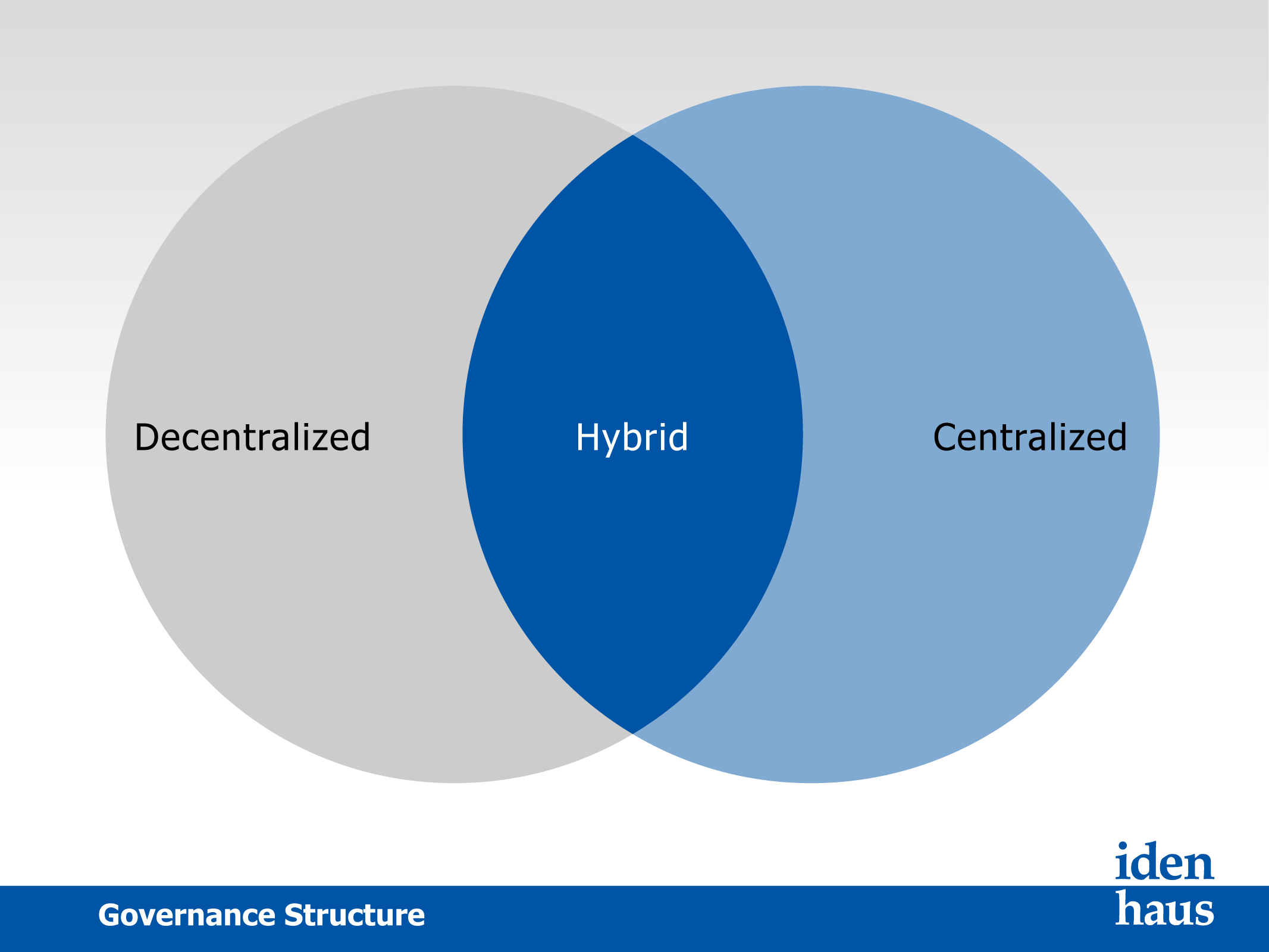
In today’s world, regardless of method or geography, people expect to access data seamlessly. The challenge is providing that access in a secure, reliable manner, and that is where IAM governance comes in. The goal of access governance is to develop a framework that incorporates standardized principles, prudent and responsible best practices, and a multidisciplinary management model that respects the diverse nature of the organization. In large and diverse communities, establishing centralized, overarching policies and standards is critical to ensure consistency among many decentralized environments and the integrity of data. A strong IAM system depends on a sustained commitment to administrative and technical privacy and security controls.
Key Deliverables:
- Recommended Access Governance structure (Centralized, Hybrid, De-Centralized)
- Define process to develop IAM policies (Security policies, naming standards)
- Define process to establish Technical Standards
- Define process to prioritize future IAM opportunities
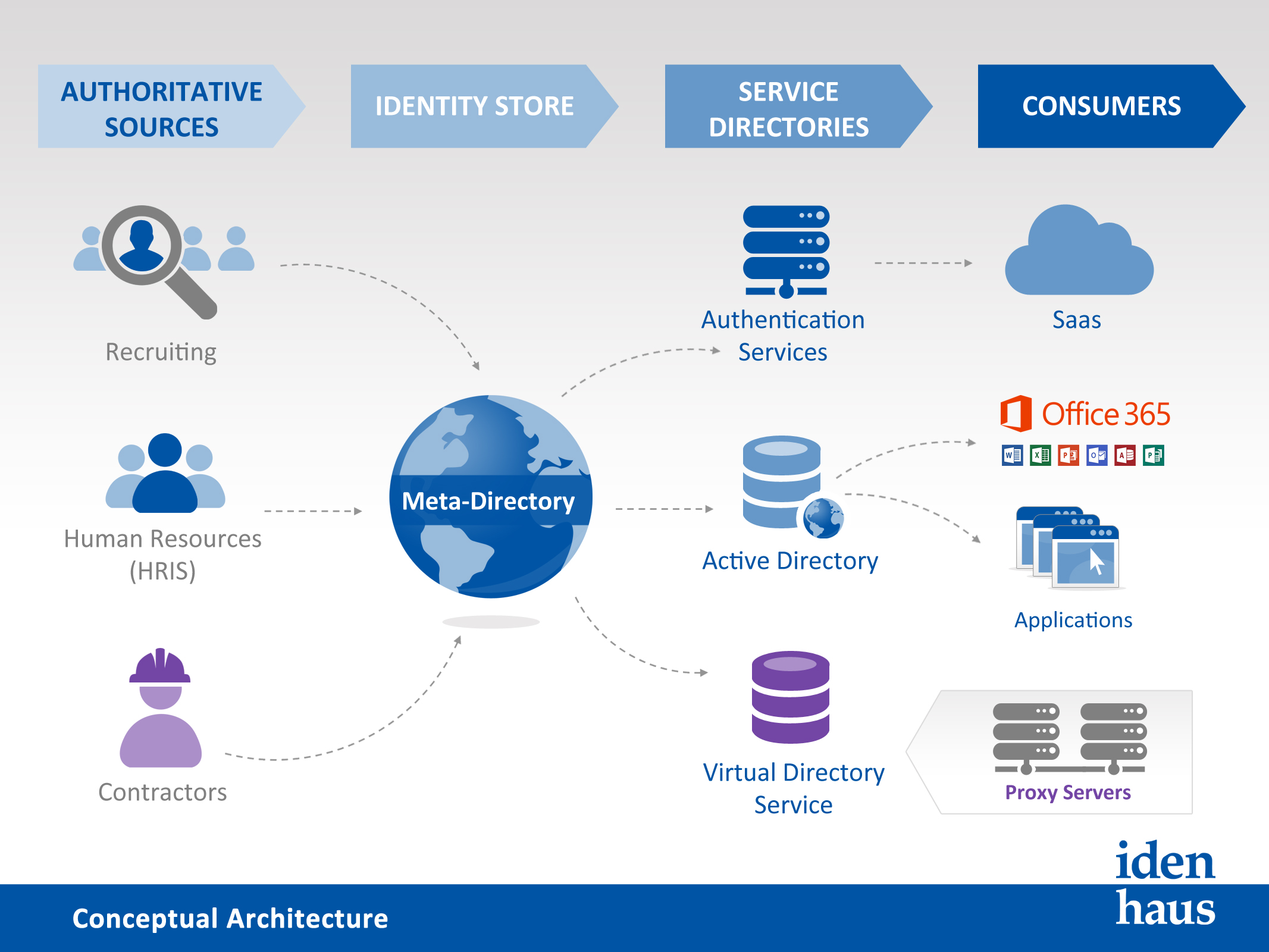
IAM Architecture & Design
We have experienced consultants who have helped many customers define the right architecture for their organizational needs. We will work with you to understand your requirements and define the necessary hardware, software, security, networking, and resourcing to build and operate your identity and access management solution effectively
Schedule your IAM / Governance Assessment
Schedule Your IAM Assessment
Subscribe to our Newsletter
Our Latest Tweets
Utilizing CSF to Manage Cyber Risks - via MedTech Intelligence @MTI_editor
Are Passwordless Systems The Future Of Authentication? via @TechRadar
5 Easy Ways To Boost Your Cybersecurity Protection via NH Business Review